Role-based access control using Amazon Cognito and an external identity provider | AWS Security Blog
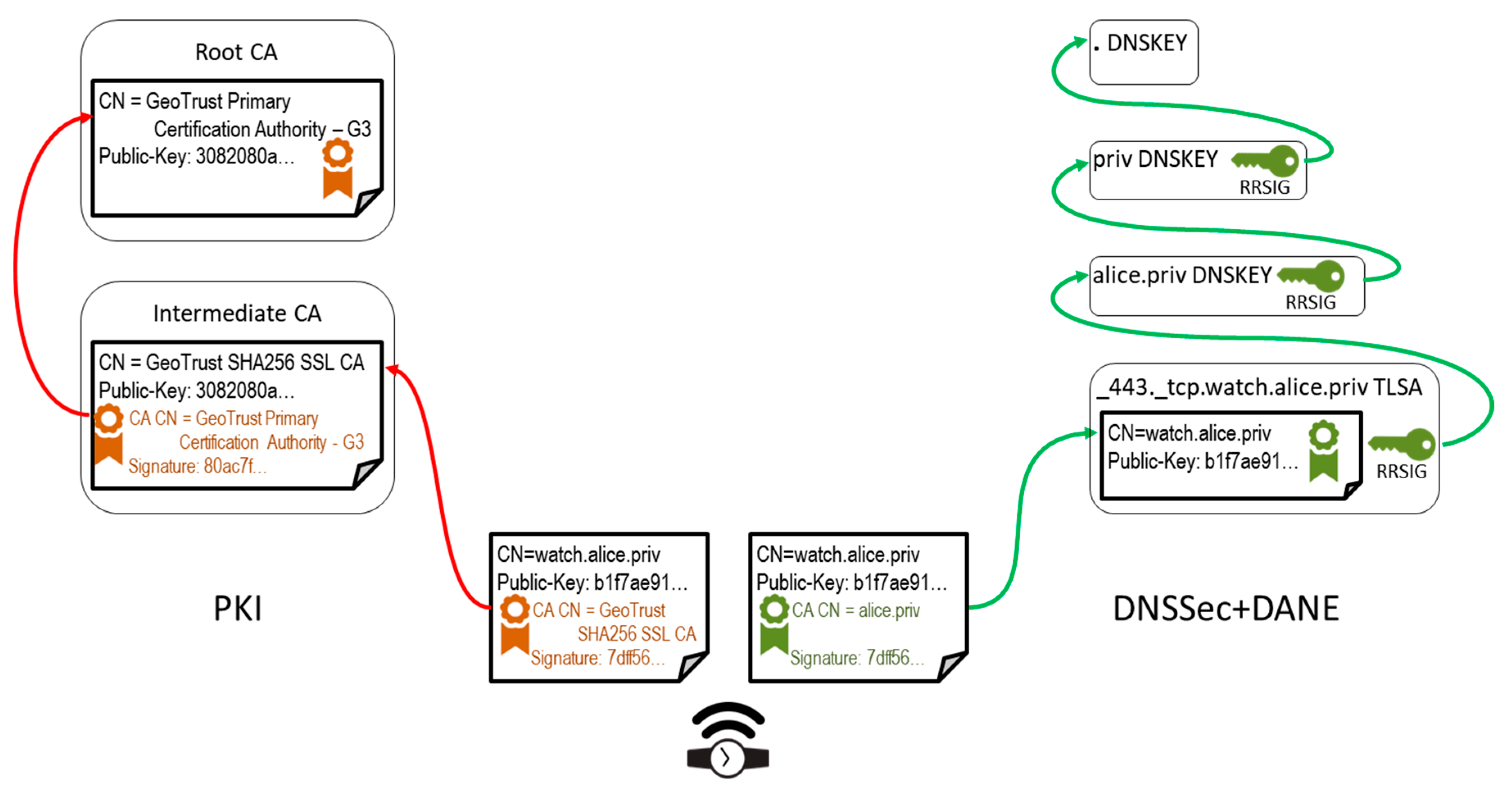
Sensors | Free Full-Text | Internet of Things with Lightweight Identities Implemented Using DNS DANE—Architecture Proposal

Scripting Your Digital World: Python is King! | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

Role-based access control using Amazon Cognito and an external identity provider | AWS Security Blog
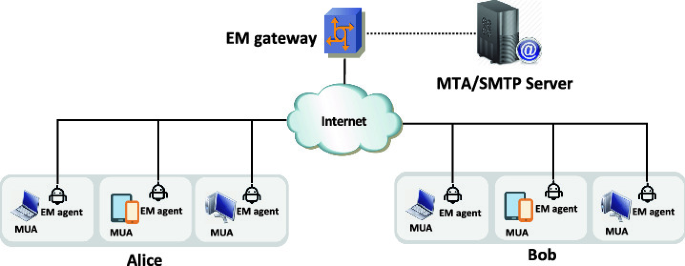
Email Address Mutation for Proactive Deterrence Against Lateral Spear-Phishing Attacks | SpringerLink

Role-based access control using Amazon Cognito and an external identity provider | AWS Security Blog